Networkings
Notes on Networkings, OSI model, TCP/IP, UDP, Sockets, etc.
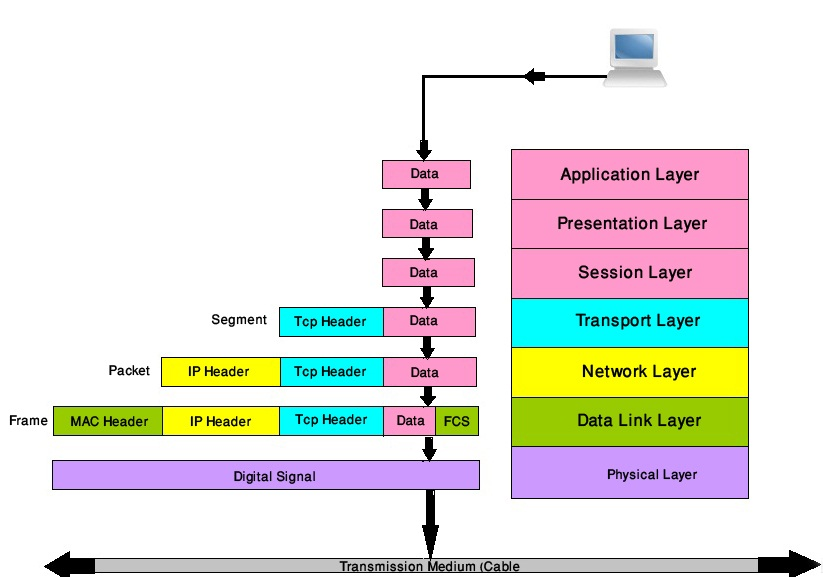
OSI Model
The OSI (Open Systems Interconnection) model is a conceptual framework used to understand and implement network protocols in seven layers. Each layer serves a specific function and communicates with the layers directly above and below it. The seven layers of the OSI model are:
| Layer | Name | Protocol | Function | TCP/IP Model |
|---|---|---|---|---|
| 7 | Application | HTTP, FTP, SMTP | Provides network services directly to user | Application |
| 6 | Presentation | SSL, TLS | Translates data formats, encryption, compression | Application |
| 5 | Session | NetBIOS, PPTP | Manages sessions between applications | Application |
| 4 | Transport | TCP, UDP | Host to host, flow control | Transport |
| 3 | Network | IP, ICMP | Determines how data is sent to the | Internet |
| 2 | Data Link | Ethernet, PPP | Handles error detection and correction from the physical layer | Network Access |
| 1 | Physical | Ethernet, Wi-Fi | Transmits raw bit stream over the | Network Access |
FIX protocol
The Financial Information eXchange (FIX) protocol is an electronic communications protocol initiated in 1992 for international real-time exchange of information related to securities transactions and markets.
Format
A FIX message is a series of key-value pairs, where each key is a tag number and the value is the corresponding data. Below is an example of a simple FIX message:
8=FIX.4.2|9=176|35=D|49=CLIENT12|56=BROKER12|34=215|52=20100225-19:41:57.316|11=12345|21=1|55=IBM|54=1|60=20100225-19:41:57.316|38=100|40=2|44=150.25|59=0|10=128|
In this example, each key-value pair is separated by a pipe (|) character. The tags represent different fields in the FIX protocol, such as:
8: Begin String9: Body Length35: Message Type49: SenderCompID56: TargetCompID34: MsgSeqNum52: SendingTime11: ClOrdID10: CheckSum
Common Message Types
D: New Order - Single8: Execution ReportF: Order Cancel Request9: Order Cancel/Replace Request
SBE (Simple Binary Encoding)
SBE is a binary encoding format designed for high-performance messaging in financial systems. It is used to encode FIX messages in a more compact and efficient manner, reducing latency and improving throughput.
Example of SBE:
// Example SBE message structure
struct Order {
uint32_t orderId; // 4 bytes
char symbol[8]; // 8 bytes
char side; // 1 byte (B for Buy, S for Sell)
uint32_t quantity; // 4 bytes
double price; // 8 bytes
};
This structure represents a simple order message with fields for order ID, symbol, side (buy/sell), quantity, and price. The total size of this message would be 25 bytes, making it much more efficient than a text-based FIX message.
Pro and Cons of SBE:
- Pros:
- Reduced message size
- Lower latency
- Higher throughput
- Cons:
- More complex to implement
- Less human-readable
- Requires schema management
Protocol Buffers
Protocol Buffers (Protobuf) is a language-neutral, platform-neutral, extensible mechanism for serializing structured data. It is used to define how data should be structured and provides a way to encode and decode this data efficiently.
Kernel Bypass
Kernel bypass is a technique used to improve the performance of network applications by allowing user-space applications to access hardware resources directly, bypassing the operating system kernel. This reduces the overhead associated with context switching and system calls, leading to lower latency and higher throughput.
Benefit of kernel bypass:
- Ultra-low latency
- Reduced CPU overhead
- Greater control over network resources
Without kernel bypass, the application interact with the network driver through the following
graph TD
subgraph User Space
App[Application]
end
subgraph Kernel Space
TCPIP[TCP/IP Stack]
TUNTAP[TUN/TAP Driver]
end
subgraph Hardware
NIC[Network Interface Card]
end
App -->|System Call| TCPIP
TCPIP -->|System Call| TUNTAP
TUNTAP -->|DMA| NIC
- TUN is for IP packets (Layer 3)
- TAP is for Ethernet frames (Layer 2)
- TCP (Layer 4) and UDP (Layer 4) are handled in the kernel space
Key Technologies
-
DPDK (Data Plane Development Kit)
- A set of libraries and drivers for fast packet processing in user space.
- Provides poll-mode drivers that allow applications to directly access the NIC.
-
PF_RING ZC (Zero Copy)
- A high-speed packet capture library that enables zero-copy packet processing.
- Allows applications to receive packets directly from the NIC without copying them to kernel space.
-
RDMA (Remote Direct Memory Access)
- Allows direct memory access from the memory of one computer into that of another without involving either one's operating system.
- Used in high-performance computing and low-latency networking.
- Bypass TCP/IP stack.
-
Solarflare / OpenOnload
- A high-performance network stack that runs in user space.
- Provides low-latency and high-throughput networking by bypassing the kernel.
-
Netmap
-
eBPF / XDP (Extended Berkeley Packet Filter / eXpress Data Path)
